Supported Postgres versions
Anything on or after Postgres 12Enable Logical Replication
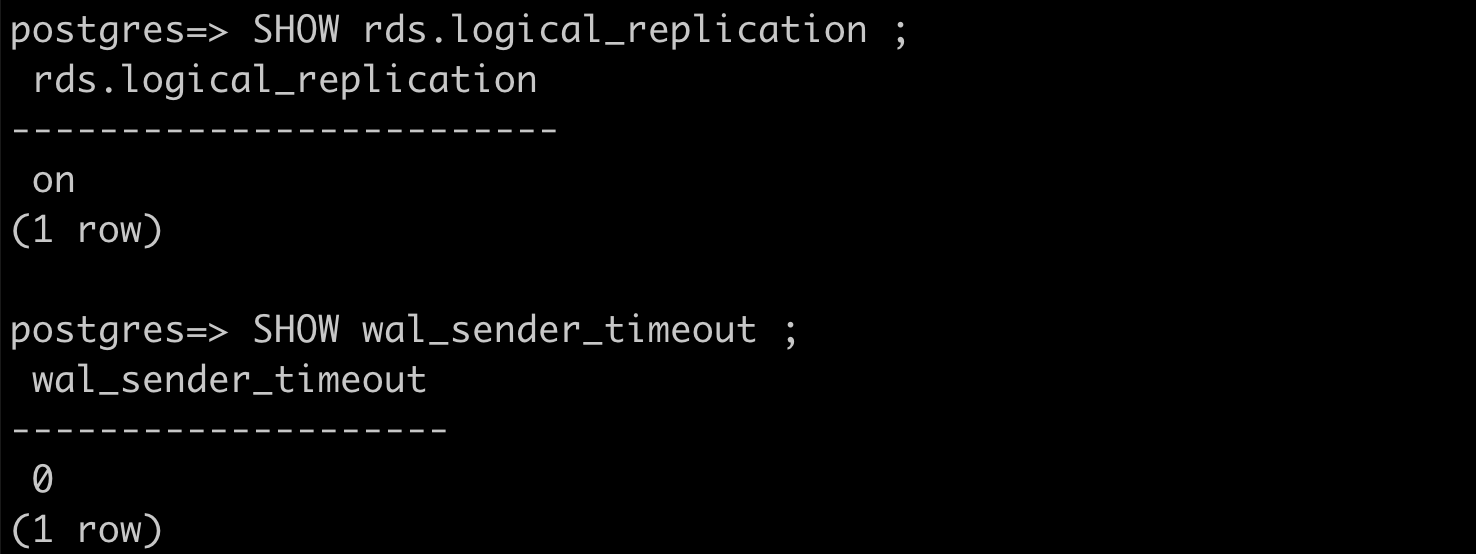
You don’t need to follow the below steps if the settingsrds.logical_replication is 1 and wal_sender_timeout is 0. These settings should mostly be pre-configured if you are migrating from another data replication tool.
-
Create a new parameter group for your Postgres version with
rds.logical_replicationset to 1; andwal_sender_timeoutset to 0.
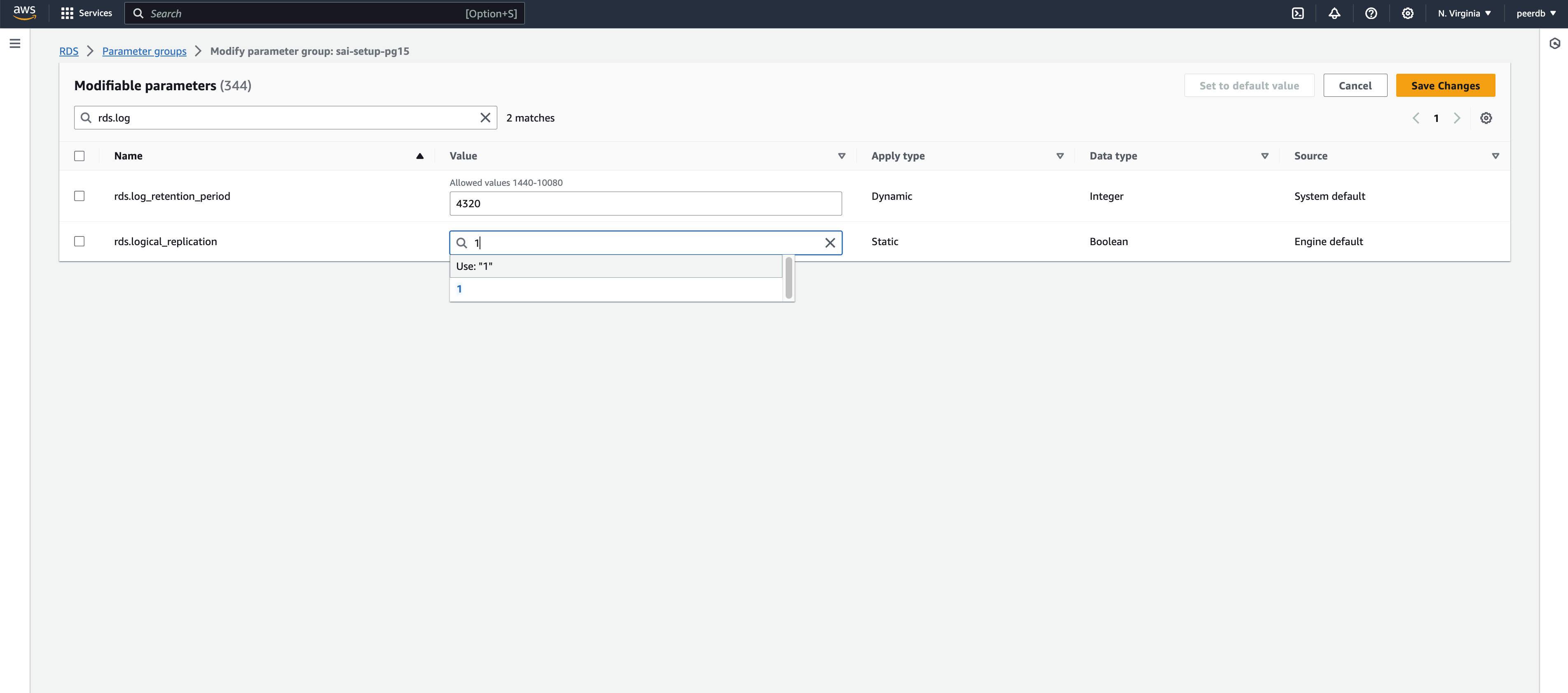
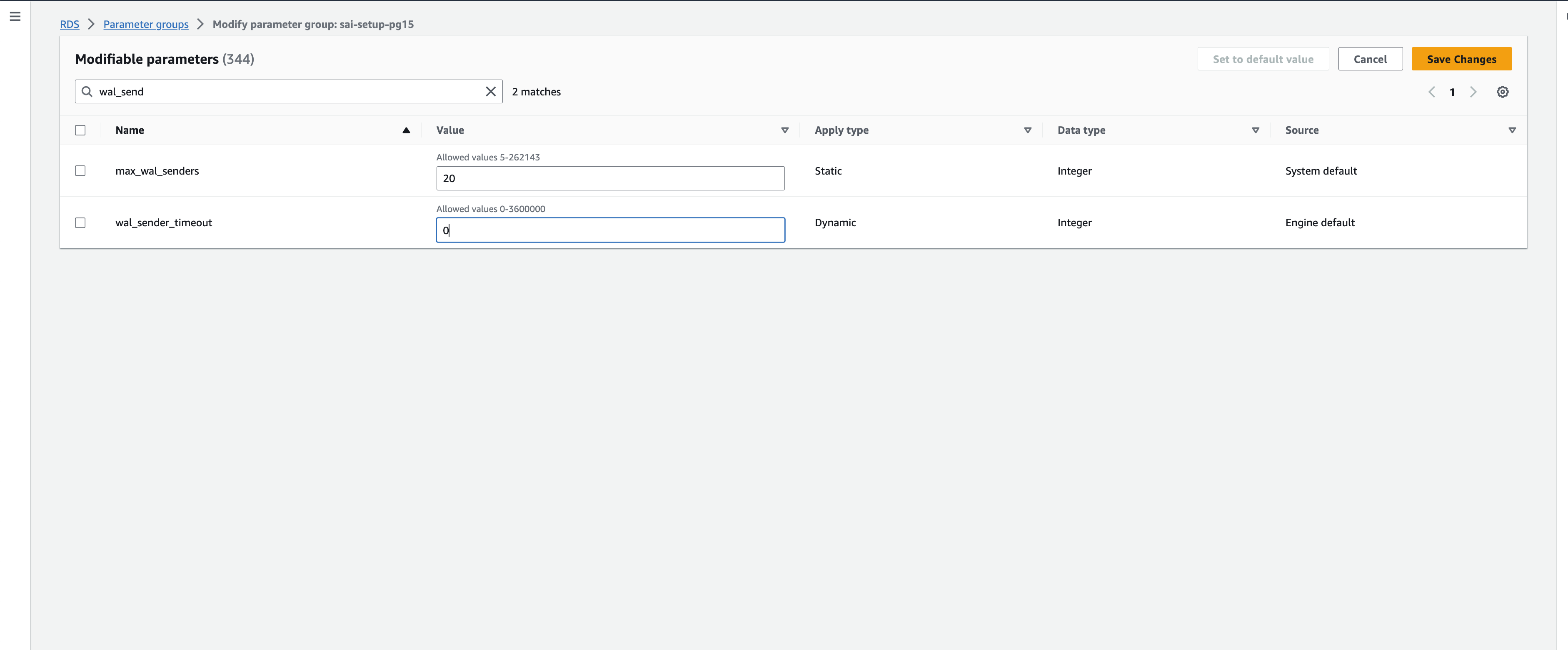
-
Modify the RDS Postgres database by adding the new parameter group.
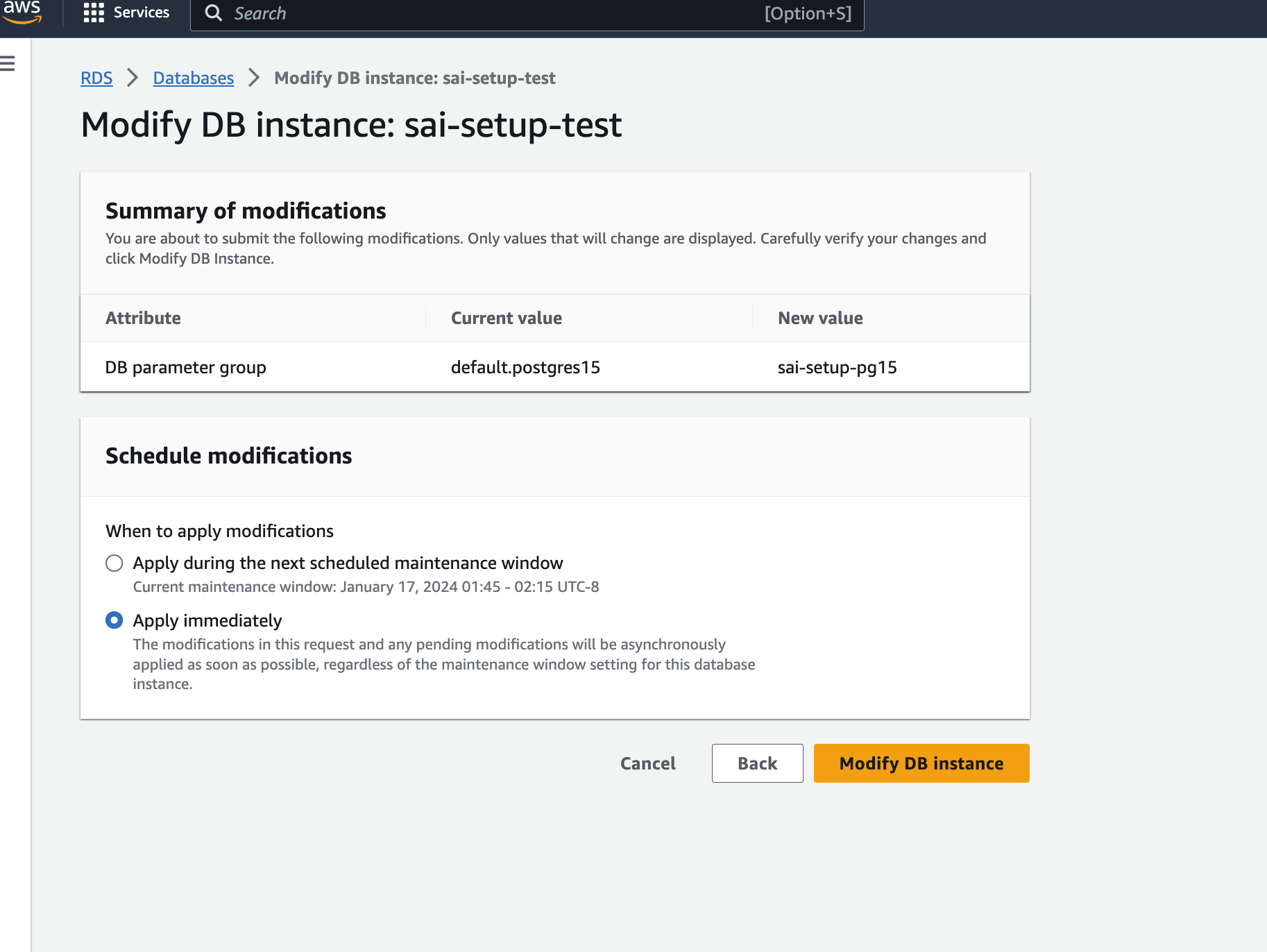
-
Reboot your RDS Postgres database for the above parameters to kick in.
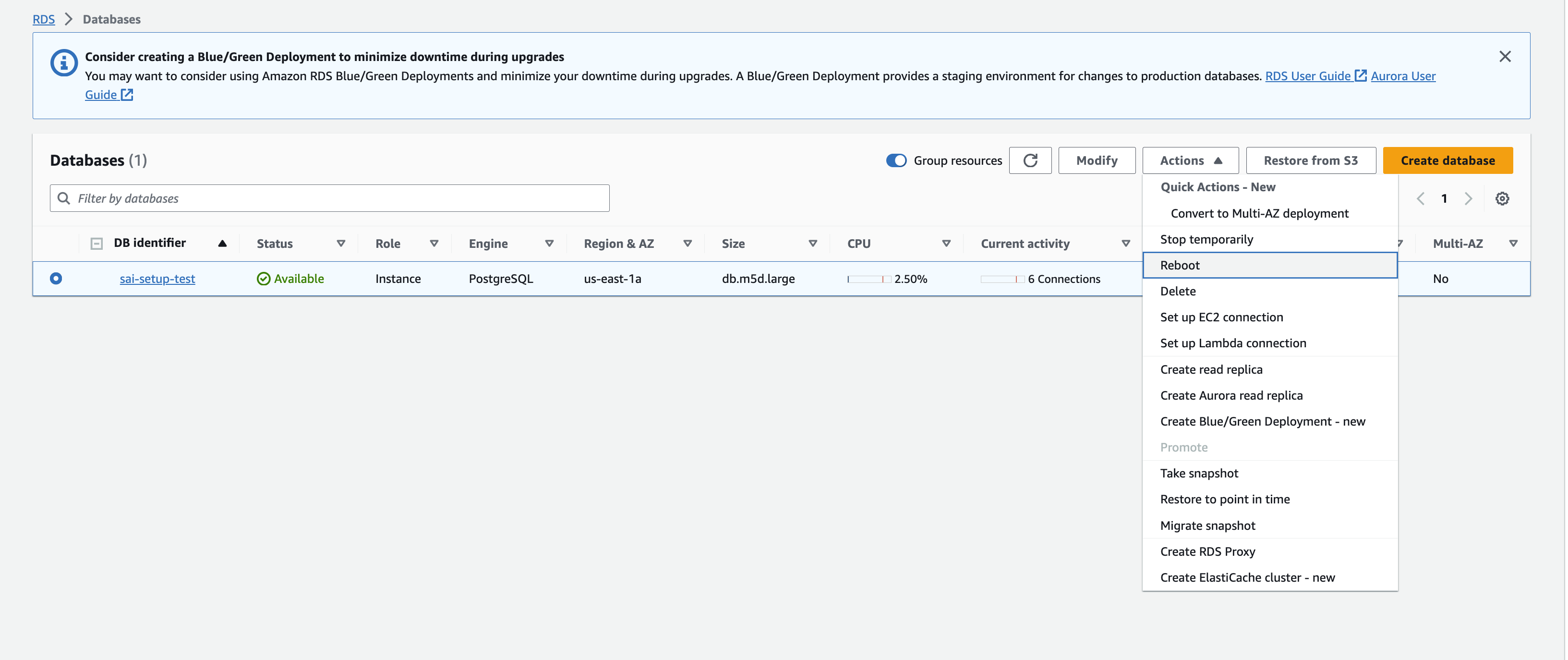
Creating PeerDB User and Granting permissions
Connect to your RDS postgres through the admin user and run the below commands:-
Create a dedicated user for PeerDB:
-
-
Grant schema-level, read-only access to the user you created in the previous step. The following example shows permissions for the
publicschema. Repeat these commands for each schema containing tables you want to replicate: -
-
Grant replication privileges to the user:
-
-
Create a publication with the tables you want to replicate. We strongly recommend only including the tables you need in the publication to avoid performance overhead.
Any table included in the publication must either have a primary key defined or have its replica identity configured to
FULL.- To create a publication for specific tables:
-
To create a publication for all tables in a specific schema:
peerdb_publicationpublication will contain the set of change events generated from the specified tables, and will later be used to create the MIRROR (replication).
The PeerDB user must not be restricted by RLS policies, as it can lead to missing data. You can disable RLS policies for the user by running the below command:
PeerDB SSH Tunneling Guide (Optional)
Sometimes to connect to your Postgres database you may need PeerDB to use an SSH tunnel. This is typically used when your database is not publicly accessible and you need to connect to it a jump server in your VPC. This is done by creating an SSH tunnel to your jump server and then connecting to the database through the tunnel. All of this is handled by PeerDB natively.Generate a key-pair
Generate a key-pair using the following command:This will generate a private key (
peerdb_key.pem) and a public key (peerdb_key.pub).Add public key to your jump server
Add the public key to your jump server. This can be done by adding the public key to the
~/.ssh/authorized_keys file on the jump server.Safe list PeerDB Cloud IPs
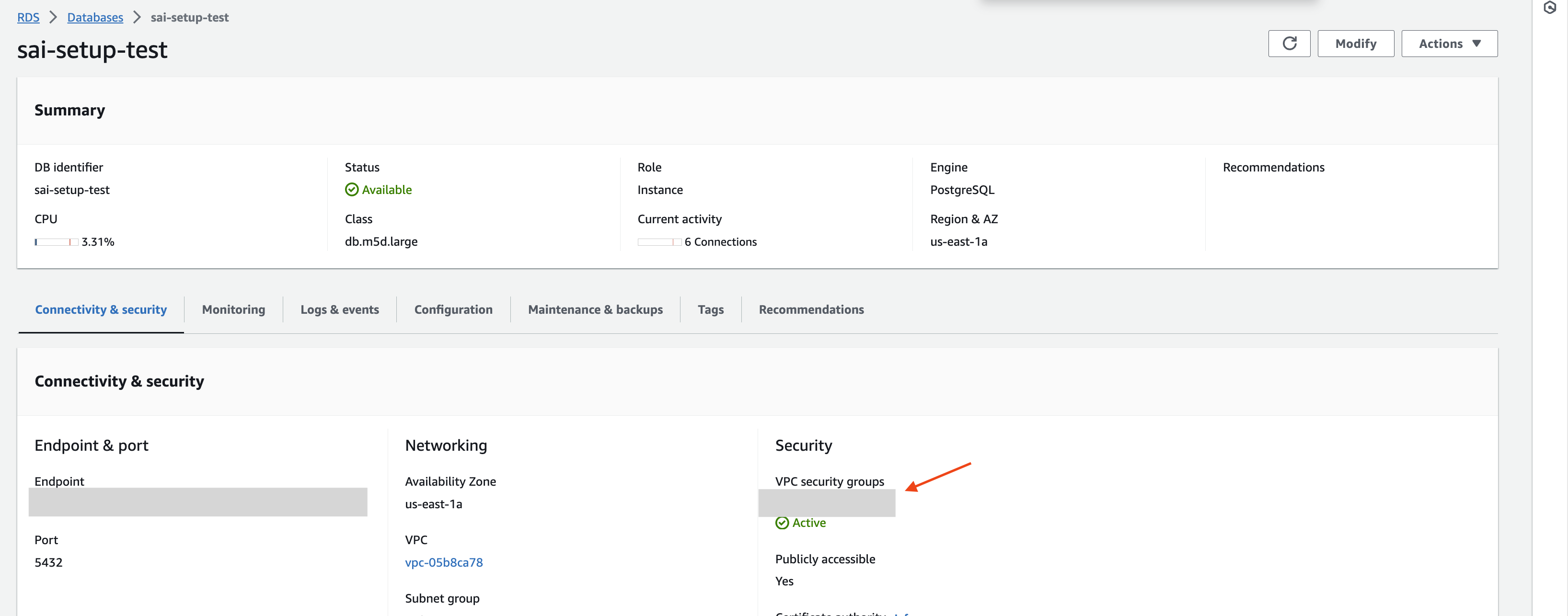
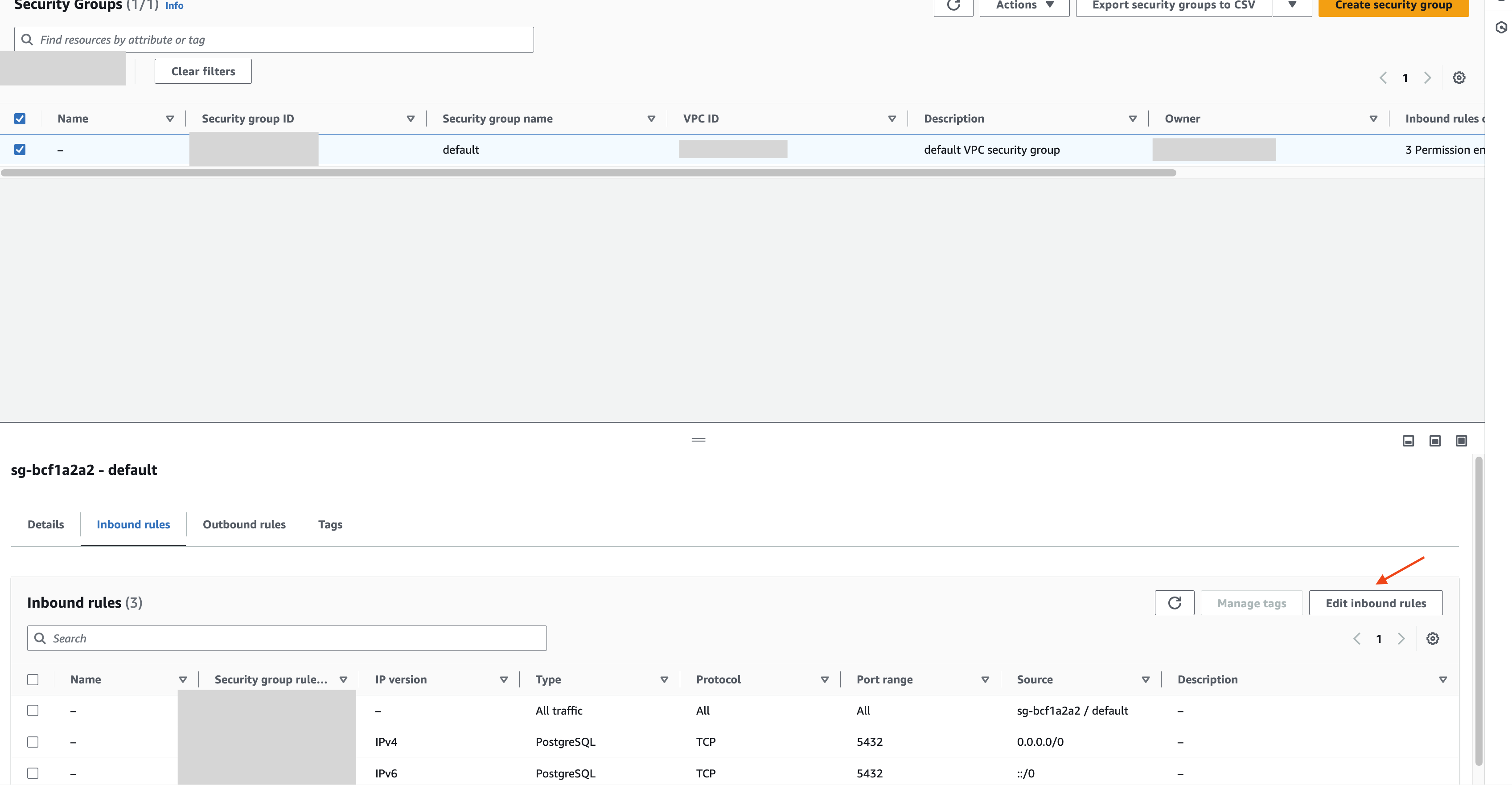
If you are using PeerDB Cloud safelist public IPs of your PeerDB Cloud instance by editing theInbound rules of the Security group in which your
RDS Postgres (OR the Jump Server/Bastion if you are using SSH tunneling) is located.
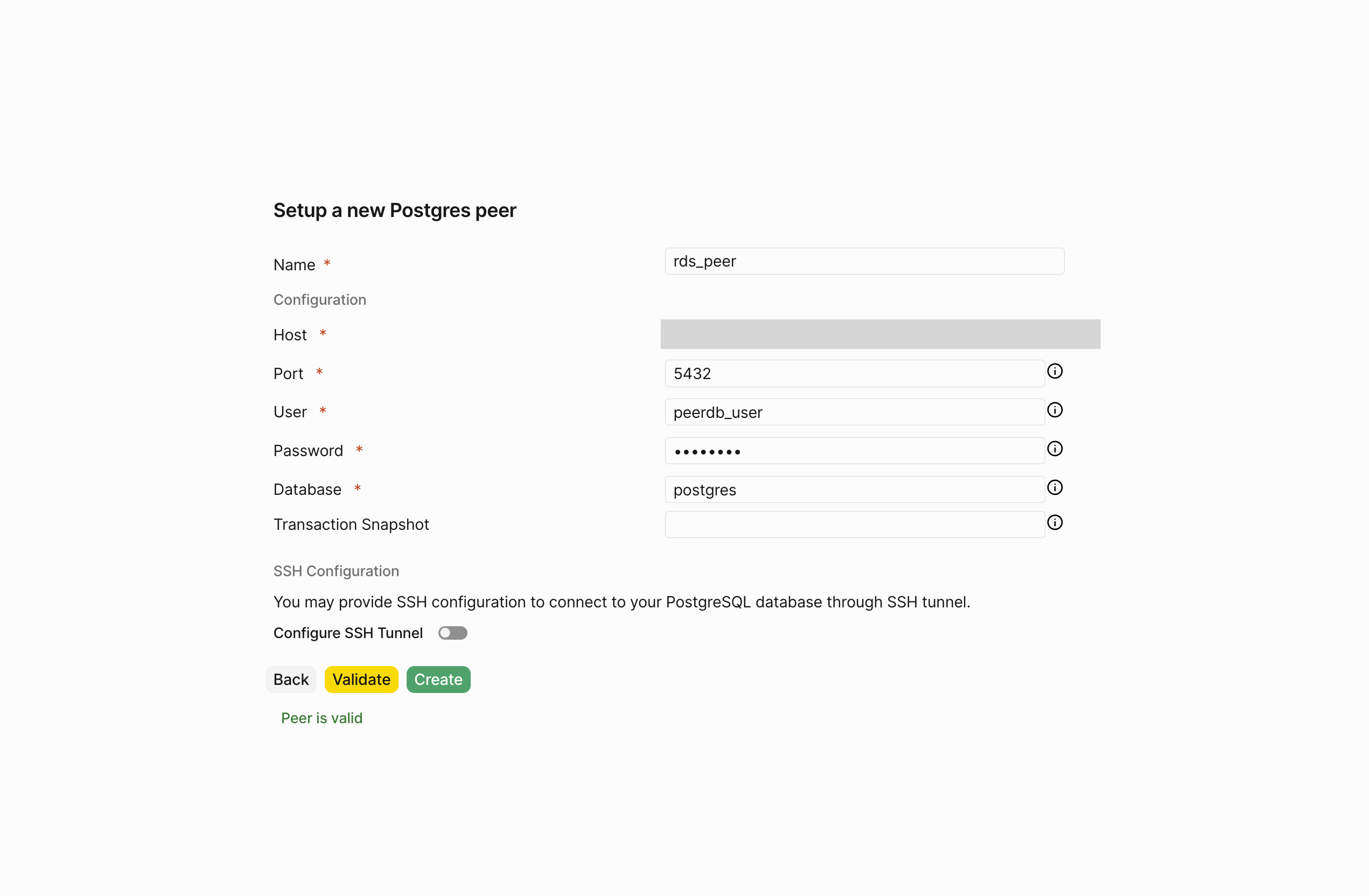
Create RDS Postgres Peer in PeerDB
Through the PeerDB UI, create the RDS Postgres Peer using thepeerdb_user that you created in the previous step.